👋🏼 CISOs: Attend GartnerSEC to gain insights on how you can: ➡️ Prepare for change in the cyberthreat landscape ➡️ Overcome the barriers of organizational culture ➡️ Balance the increasing variety of cybersecurity decisions Explore the agenda: CISO
Keynote: Debunking the Myths that Obscure Cybersecurity's Full ValueCybersecurity can generate massive value for our enterprises, but only if we have the courage to challenge the lies that we as cybersecurity professionals tell ourselves. Our self-deceptions lock us into obsolete principles and practices that prevent us from truly aligning with our executive partners and enabling our organizations.
We like to lament that "the users are the weakest link in the cybersecurity chain," which means that as security and risk management leaders, you must understand the critical impact of the user community on your programs. From basic anti-phishing simulation through more proven communications techniques to sophisticated approaches based on social science, this presentation provides insight into the latest best practices in the human aspects of security.
Please Note: Based on availability and eligibility you may sign-up for the session via Conference Navigator after you register for this conference.Roundtable: Security Organizational Structure Planning & DesignEver struggle with designing a security function that is appropriate for your organization? Join us for an interactive roundtable to discuss the different approaches to structure your cybersecurity function through examples.
Please Note: Based on availability and eligibility you may sign-up for the session via Conference Navigator after you register for this conference.How Do Ethnicity, a Life of Public Service and Cultural Background Enable Security?Attendees will discuss the impact of the lack of diversity in decision making, testing and validation, and workforce retention.
Please Note: Based on availability and eligibility you may sign-up for the session via Conference Navigator after you register for this conference.How to Respond to the Evolving Threat Environment, 2023The threat landscape is a moving target. Attack campaigns might hit multiple organizations, but each enterprise should analyze its own threat landscape.
Risk appetite fails when expressed in fuzzy, imprecise terms. Repositioning risk appetite in the context of investment and value delivery creates a measurable scale of risk that powers a new type of governance. Concrete assertions of risk appetite make executive decisions binding.Don't Let Your AI Control You: Manage AI Trust, Risk and SecurityAI teams are perceiving risk differently than security teams.
This session will present an overview of the latest version of the Magic Quadrant for Endpoint Protection Platforms . Participants will hear about Gartner's methodology, research highlights, key market trends and vendors.Integrating SASE, XDR and Other Security Vendor Consolidation Trends in Security StrategyA number of consolidation trends, such as SASE and XDR, and also CNAPP and DSP, are beneficial to reduce enterprise security complexity.
This session will outline the current state and emerging trends in the market for privileged access management.Jon Amato, Sr Director Analyst, Gartner Zero trust network architecture in the federal space must meet particular requirements. Attendees will get exposure to those requirements and variables surrounding the federal space, ranging from administrative and development networks to tactical systems.Patrick Long, Sr Principal Analyst, GartnerLearn about what's important to midsize enterprises in cybersecurity.
Please Note: Based on availability and eligibility you may sign-up for the session via Conference Navigator after you register for this conference.Eric Grenier, Director Analyst, GartnerEndpoint security tools have evolved from protection-only tools to foundational building blocks of XDR strategy. Gartner's Endpoint Security analysts have invited a select group of endpoint security vendors to showcase their products in action.
Please Note: Based on availability and eligibility you may sign-up for the session via Conference Navigator after you register for this conference.Having the BYOD Security - and Privacy - ConversationSecurity and privacy can effectively co-exist on personal devices to a degree never before possible, but privacy implications remain. This session explores effective security controls and their implications for security and privacy.
Leaders responsible for IAM generally focus on the technical benefits of an IAM solution rather than its impact on the organization's goals and objectives. They are unaccustomed to recognizing and accommodating the influence IAM has on business outcomes or associating IAM with environmental, organizational or social change. These skills are critical to an initiative with IAM's scope and breadth.
Application security continues to evolve, with DevSecOps and API security coming into maturity. However, organizations must also look to secure their software supply chain and cloud-native deployments effectively. This session will explore this evolving landscape and provide organizations with the insights they need to consider for 2023 and beyond.
Bring your questions about DLP, data discovery, data classification and data privacy of both structured and unstructured data. Security operations are undergoing a transformative change when our security is planned and delivered. Do you really need to centralize data for security? Is there a single solution to solve all my security needs? How do we determine what is threat intelligence for us? Learn what technologies, processes and services will have the biggest impact on how security operations are delivered in 2023.
Modern SOCs require proactive and automated capabilities, such as threat hunting, prioritized threat intelligence and automated response. This session will describe modern SOC core capabilities, and guide SRM leaders on how to evaluate whether their current SOC has established those capabilities and processes.Start Your Threat Exposure Management Program With These Three StepsEnterprise's attack surface expands and is fragmented across a variety of environments.
Come build a security architecture live in this session. This special session will show you how to build your security architecture from the ground up. We will all be a part of the company ACME and build our security architecture together from the ground up. This will be great for new security professionals who are just starting their architecture and seasoned professionals to get tips and tricks to modify their existing architectures.
Please Note: Based on availability and eligibility you may sign-up for the session via Conference Navigator after you register for this conference.Technical Insights: SSE 101- How to Secure Web Access, SaaS, and Private Apps With Security Service EdgeSecurity service edge is an emerging market that consolidates CASB, SWG, and ZTNA.
Please Note: Based on availability and eligibility you may sign-up for the session via Conference Navigator after you register for this conference.Technical Insights — Cybersecurity Mesh Architecture: The Next Generation of Security ArchitectureThis session will discuss the reference architecture and dive deep into how to build the cybersecurity mesh architecture . We will discuss the evolution of best of breed to the new CSMA, along with pros and cons of each approach.
This interactive "gamified" workshop is designed to actively involve senior leaders, board members and business stakeholders to boost their awareness of cybersecurity by flipping their perspectives and looking through the lens of the attacker. This workshop also provides an approach to identifying potential gaps and the actions required to bolster the security efforts of the enterprise.
Please Note: Based on availability and eligibility you may sign-up for the session via Conference Navigator after you register for this conference.CISO Circle: Research Discussion: The CISO’s Guide to Cyber Risk QuantificationIn this interactive discussion, exclusively for CISO circle participants, you'll network with peers on their cyber risk quantification efforts and discover how to use CRQ to influence business decision making.
Please Note: Based on availability and eligibility you may sign-up for the session via Conference Navigator after you register for this conference.CISO Circle Breakfast: Leadership Exchange: The Five Cybersecurity Board Questions That You Must Be Prepared to AnswerBoard members realize how critical security and risk management are and have started to ask leaders more complex and nuanced questions.
Norge Siste Nytt, Norge Overskrifter
Similar News:Du kan også lese nyheter som ligner på denne som vi har samlet inn fra andre nyhetskilder.
 Gartner Security & Risk Management Summit, Day 1 HighlightsWe hope you enjoyed Day 1 of Gartner Security & Risk Management Summit. Highlights include: ✅ Top cybersecurity predictions ✅ Outlook for network security ✅ Tips for third-party cybersecurity threats Learn more on the Gartner Newsroom: GartnerSEC
Gartner Security & Risk Management Summit, Day 1 HighlightsWe hope you enjoyed Day 1 of Gartner Security & Risk Management Summit. Highlights include: ✅ Top cybersecurity predictions ✅ Outlook for network security ✅ Tips for third-party cybersecurity threats Learn more on the Gartner Newsroom: GartnerSEC
Les mer »
 Fed raised concerns over SVB risk management as early as 2021, Michael Barr says“SVB failed because the bank’s management did not effectively manage its interest rate and liquidity risk and the bank then suffered a devastating and unexpected run by its uninsured depositors,” Fed Vice Chair Michael Barr will tell Congress Tuesday.
Fed raised concerns over SVB risk management as early as 2021, Michael Barr says“SVB failed because the bank’s management did not effectively manage its interest rate and liquidity risk and the bank then suffered a devastating and unexpected run by its uninsured depositors,” Fed Vice Chair Michael Barr will tell Congress Tuesday.
Les mer »
 Gartner Unveils Top Eight Cybersecurity Predictions for 2023-202450% of CISOs will adopt human centric design to reduce cybersecurity operational friction, according to the top cybersecurity predictions revealed by Gartner today. Learn more on the Gartner Newsroom: GartnerSEC GartnerIT security
Gartner Unveils Top Eight Cybersecurity Predictions for 2023-202450% of CISOs will adopt human centric design to reduce cybersecurity operational friction, according to the top cybersecurity predictions revealed by Gartner today. Learn more on the Gartner Newsroom: GartnerSEC GartnerIT security
Les mer »
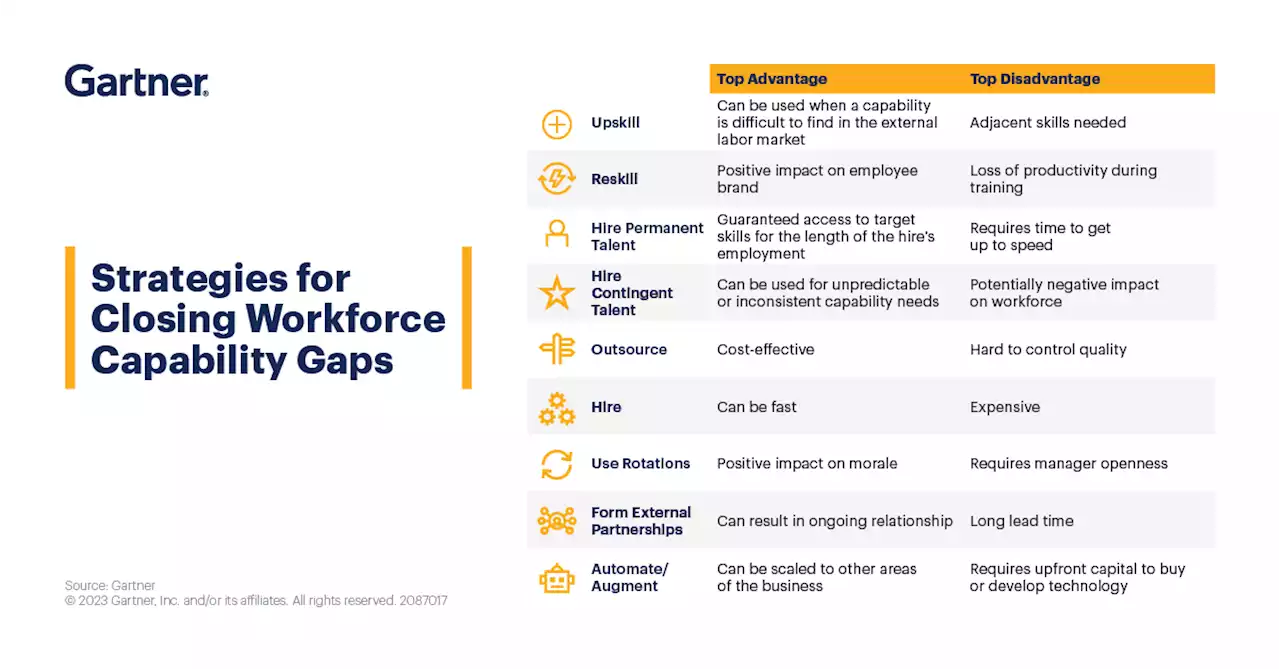 CISO Foundations: Cybersecurity Talent Strategies for CISOsTo address cybersecurity challenges, CISOs should prioritize experiential training and develop forward-looking talent strategies 💡 Here's how you can develop and retain internal talent based on their experience and feedback: GartnerSEC
CISO Foundations: Cybersecurity Talent Strategies for CISOsTo address cybersecurity challenges, CISOs should prioritize experiential training and develop forward-looking talent strategies 💡 Here's how you can develop and retain internal talent based on their experience and feedback: GartnerSEC
Les mer »
Experts say 'fake work' claims in tech are 'excuse for bad management'The notion of 'fake work' or coasting in the tech industry has a long history, but experts say it's just an 'excuse for bad management'
Les mer »
 Condo Adviser: Condo boards are not legally required to hire management companiesIn this week's Condo Adviser: 'Illinois law does not mandate that a condominium board hire a management company for any size condominium association.'
Condo Adviser: Condo boards are not legally required to hire management companiesIn this week's Condo Adviser: 'Illinois law does not mandate that a condominium board hire a management company for any size condominium association.'
Les mer »
